Shellshock – The Bash Bug That Can Be Exploited With Three Lines Of Code
 Eqservers
Eqservers EqServers News
EqServers News 28/09/2014
28/09/2014
Shellshock or the Bash bug is a new security flaw in most Linux and Unix based operating systems. Due to the widespread use of Bash, the bug can compromise anything from major servers to an internet enabled fridges and a majority of other connected devices that use Bash.
The new bug (assigned ID: CVE-2014-6271 ) lets hackers run unauthorized code through Bash, a standard program built in Linux and Unix to connect with the host machine’s OS. As demonstrated by security experts, it’s quite easy for hackers to identify and break into vulnerable machines. Initial investigation reports suggest that Mac may also be vulnerable as it makes use of Bash.
Once compromised, attackers can take over the victim machine and access confidential information or make changes to it. They can also use the compromised machine to take complete control over other connected machines on the same network. That’s why it has been rated 10 for severity. The severity 10 is used to denote maximum impact. It is a problem that needs immediate attention.
While some businesses are still recovering from Heartbleed, the bug has been identified recently. It is being compared with the Heartbleed. In reality though, it is much worse than Heartbleed bug because Shellshock could cause havoc on much larger scale across the globe. It appears to be capable of opening the flood gates for attackers into large networks.
It has been established by some security experts that due to the way Internet works, all connected machines may be directly or indirectly affected. At the time of writing this blog, no break-ins related to Shellshock have been reported. However, security experts believe that the vulnerability can be exploited with just three lines of code and hackers will be tempted to write scripts that can jump from one vulnerable system to another and create a worldwide havoc for system admins and security experts.
The good news is that, it may be easy to fix. There are reports that a combination of software patch and Web Application Firewall (WAF) rules may be able to defend your dedicated servers. Most operating system vendors and Linux distributions have released an update today but those updates have been unable to fully mitigate the risks. As always, the best protection is to update. Keep an eye on the next update from your OS vendor or from your Linux distribution and install it as soon as it becomes available.
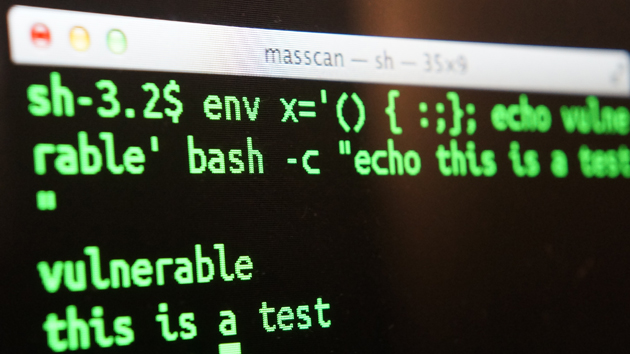
- To check if your machine is vulnerable, run the following command within the shell:
- env X=”() { :;} ; echo busted” /bin/sh -c “echo completed”
- env X=”() { :;} ; echo busted” `which bash` -c “echo completed”
- If you see “busted” then the machine is vulnerable. The fix is to patch the system in a way that – any kind of code is not allowed to execute at the end of a Bash function.
At Eqservers, we are constantly monitoring the situation and we will do our best when more information is available.